IP address determines your identity online. But what happens if an intruder uses it to their advantage? Apart from stealing your personal information, they can monitor your internet traffic and commit serious cybercrimes using your name. IP spoofing refers to such cyberattacks. In this post, you will learn how hackers use this tool and how you can protect yourself.

IP Spoofing: What It Is?
The technique through which hackers replace the original IP address of a user with a fake one is referred to as IP spoofing. Because of IP spoofing, the internet traffic appears to come from a legal source. Besides, hackers can use this tool to mask the IP address of the receiver as well. Let’s learn how IP spoofing works when you are online.
First, your internet traffic consists of several packets that receive and send information over the web. Every data packet is sent separately and gets collected at the destination. For example, the destination could be the servers of the website or the device of the receiver. Each data packet comes with IP headers. They contain details about the IP address of the receiver and the source. The data packets use TCP/IP protocol during transmission.
However, the TCP/IP protocol comes with a disadvantage. This protocol has to perform a 3-way TCP handshake. That way, it transfers data from one party to another. Let’s understand it in detail.
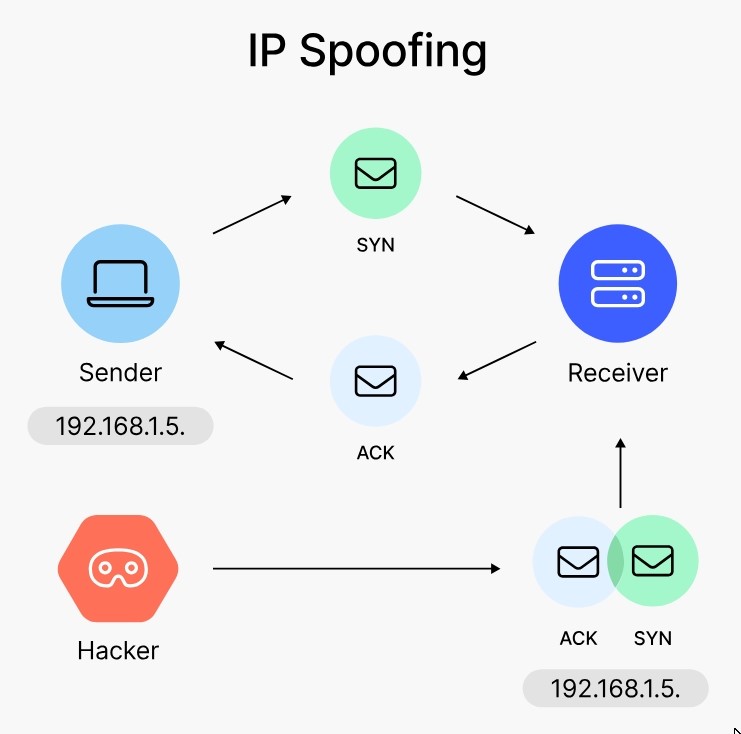
- Step – 1: The receiver gets a SYN message from the source. The message builds a connection between two devices. Also, it synchronizes the sequence numbers of the devices.
- Step – 2: The source gets an ACK message from the receiver. It’s an acknowledgment from the receiver’s end.
- Step – 3: The receiver gets a SYN-ACK message. It means that the connection is secure.
IP Spoofing: How It Works?
During IP spoofing, the hacker interrupts the handshake just before the completion of the third step. This is when the source is about to send the SYN-ACK message to the receiver. The hacker generates a fake confirmation about the connection and the device address. Also, they send a spoofed IP address representing the main sender. What happens is that the receiver believes that the main sender built the connection. In reality, they are interacting with a compromised IP and have been victims of IP spoofing.
IP Spoofing: The Dangers Involved
These days, hackers come up with intuitive strategies to use IP spoofing. They use it to intercept individual users’ data, servers, or other applications. Below are the important and most common uses of a spoofed IP.
-
Evades firewalls and even IP authorization
The most common use of IP spoofing comes in the form of security breaches. This tool can bypass security measures like firewalls effectively. As you know, firewalls work by blocklisting. However, a hacker who is spoofing IP addresses can bypass firewalls even if their real IP address has been blocked.
Hackers using spoofed IPs can interpret systems that come with allowlists as well. Typically, these systems allow communication between trusted IP addresses. A hacker can manipulate a trusted IP and can easily become a part of a computer network. They can explore and cause problems later. It is wise for companies not to depend on IP authorization solely. Rather, they should try alternate methods for IP authorization.
-
DoS attacks
In the case of a DoS (Denial of Service) or DDoS (Distributed Denial of Service) attack, excessive fraudulent requests bring down a website or server. The botnet worms infect the devices to carry out these requests. Even the system owners are unaware that they are helping the hacker.
Besides, hackers use IP spoofing to alter fraudulent communications. They send tons of fraudulent requests for files while spoofing the IP addresses. As such, the servers have to send responses to every device on a network.
-
MITM attacks
The MITM or man-in-the-middle attack is another kind of cyberattack where a hacker becomes the middleman between two parties. They intercept and use information between an application and a user. The hacker pretends that they represent both the website and the user. They fool both parties. This kind of attack is common in public Wi-Fi networks.
In an MITM attack, the information you share is not safe because the hacker gathers data by sitting there. The information you are sharing might not appear unsafe at the moment. But they can break into your account later. The best way out of it is to use a VPN.
IP Spoofing: Is It Illegal?
Spoofing IP addresses is not considered illegal as long as someone does not use the data for personal gains. For example, users can choose a VPN or proxy service to hide their real location. And, browse the internet privately and securely. Besides, website admins create plenty of fake visitors online by using IP stressers. They need to conduct stress tests for their servers or websites.
IP spoofing is illegal when a bad actor uses the IP address of someone else to perform cybercrimes like identity theft.
IP Spoofing: How Do You Prevent Yourself?
Finding a spoofed IP address is almost impossible. Even if you detect it after some time, the damage could have been done. Still, there are a few tips on how to protect yourself from hackers that use spoofed IP addresses.
- Always use a robust method to verify identity
- Monitor the network for a specific activity
- Use IPv6 instead of IPv4
- A firewall should guard a considerable amount of computing resources
- Try using DPI or Deep Packet Inspection
- Implement data egress and ingress filtering
It is nearly impossible for an ordinary user to detect IP spoofing. But anyone can minimize the vulnerabilities by following these tips.
- Visit HTTPS websites that have VPNs – Certain websites run on TLS/SSL protocol. It means that the connection is encrypted and secure.
- Use a reliable VPN – A reputable VPN service encrypts your traffic and makes it difficult for hackers to monitor your activities online. VPNs prevent hackers from spoofing your IP addresses, too. Moreover, a reliable VPN protects you from compromised sites where the chances of IP spoofing are high.
- Install antivirus – even if someone spoofs your internet traffic, a good antivirus software can detect it easily. The antivirus scans data packets to detect malicious code if there is any. Remember that installing an antivirus is not the ultimate solution.