In the past, people accepted surveillance with little resistance whenever questioned. They were not concerned about being monitored because they believed they were not doing anything wrong. But now, the overwhelming presence of tracking technologies and tech-driven innovations has shifted the conversation around surveillance. All forms of technology collect user data, from smart meters and mobile devices to web browsers. The information is shared with third parties or analysed to develop consumer profiles for targeted marketing.
Privacy was once regarded as a fundamental right, widely respected across many countries. Changes to rules and regulations were rare. Besides, they were typically introduced to benefit the whole society.
Although things have changed a lot, the impact has been negative.
Government surveillance, ISP-level censorship, widespread data collection, and attacks on encryption are all privacy threats. Meanwhile, constant cyberattacks on individuals and organisations are on the rise more than ever. These challenges are turning privacy into a privilege for the few, rather than a basic right for all.
Modern-day services and products can compromise your security and privacy. Moreover, you cannot trust the security regime that vendors offer or the constantly changing surveillance techniques.
These days, everyone using the internet should safeguard their online privacy from companies, the government, and from one another.
The steps outlined below can provide you with some protection against the growing threat of surveillance tactics. Additionally, they will help safeguard you from cyberattacks, scammers, online stalking, and other digital dangers.
Personal identifiable information: What is it and why does it matter
Personal identifiable information, or PII, contains important information about you. These include your name, date of birth, home address, telephone numbers, email address, Social Security numbers, marital status, and other IDs. Besides, PII can include information on your employment status, children, family members, and medical records.
What if the information gets lost in data breaches or stolen via phishing strategies? It will provide cyberattackers with adequate information to steal your identity. In short, an intruder will take advantage of your identity to engineer social media attacks. Also, you cannot access your online accounts. Most importantly, you may have to deal with any kind of financial fraud.
The information is enough for a cybercriminal to take out loans or make forged transactions in your name. Even if the information falls into the hands of advertisers, it will be a gold mine for them.
Why should you care about your online activity and the sites you visit?
An ISP (Internet Service Provider) can monitor your internet activity. It means the information could be hijacked. Unfortunately, consumers have few options for protection when it comes to ISP-level attacks. Moreover, cookies can track the websites you visit. Cookies are small pieces of text that your browser downloads and stores locally. Additionally, browser plugins can monitor your activity online.
Cookies customise your online experience, including personalised advertising. However, this type of tracking can become invasive. Unique identifiers embedded in cookies are often shared across services and marketing platforms. As such, it allows third parties to follow users across the web.
For example, search for a smart TV and spend some time on the internet with it. You will likely be flooded with smart TV advertisements. This is how organisations target users.
Why should you protect your messages and emails?
An email is a useful tool that helps you connect to other important accounts, be it social media or banks. An email also contains a record of your communication with colleagues, friends, and family. But hackers can get your email ID and password via phishing scams, social engineering, or credential stuffing. They can access other services that are linked to your email.
Most people use a single email for multiple services. As a result, hackers can use this information to access other services and accounts linked to the email. For instance, your primary email account is commonly associated with services such as your mobile carrier or preferred shopping sites. An attacker can modify your login credentials or steal the verification code needed to access your account.
Why should you keep your phone numbers private?
During targeted attacks, cybercriminals may employ social engineering tactics to pose as their victims when contacting phone service providers. Scammers do this to temporarily move the victim’s phone number to a different device. They can receive the 2-factor authentication codes sent to that number during that period. This allows them to gain access to accounts.
With access to these codes, attackers can break into sensitive accounts. These include email, banking, or cryptocurrency wallets. As such, it put victims at serious risk of financial loss and identity theft. These attacks are called SIM-swapping.
If someone gains control of your phone number, they can intercept 2-factor authentication codes. Ultimately, it will put any account linked to that number at risk of being compromised.
Why should you protect your financial information and online purchases?
When you make a transaction online, sensitive information is often shared. This can include login details for services like credit card data or PayPal, such as the card number, expiry date, and security code.
However, scammers target vulnerable e-commerce sites. They inject a code into payment portals so that they can steal information on the card set by the user. As a result, cybercriminals intercept your information without your knowledge. In short, you are completely unaware that your valuable information has been compromised.
Cybercriminals steal your financial information through fraudulent websites and phishing. They intercept the data through a middleman, or someone who uses card-skimming malware. They can easily steal the details when the data is less secure.
After accessing the information, criminals generate clone cards to launch unauthorised financial transactions. Sometimes, they sell the information on the dark web to interested parties.
If your card details are compromised, it can result in fraudulent purchases made on your behalf. Therefore, if you notice suspicious transactions or even small payments in succession, it is time for you to act.
Get in touch with your bank immediately to report the issue and prevent further unauthorised activity. Request a freeze or cancellation of your card, and consider ordering a replacement. Additionally, review your credit report for any suspicious activity or new accounts you did not authorise.
Why should you protect your medical reports and DNA profiles?
These days, hospitals have adopted the new way of recording medical reports electronically. Besides, home DNA services have been popular lately. Genetic information of a patient can be stored, collected, and submitted for queries related to health or to trace family history.
Hence, losing medical information can be unsettling and cause a lot of discomfort. Sometimes, it might have severe consequences for people involved.
However, when it comes to DNA profiles, you can choose whether or not to release the information. Even if the demand is from concerned authorities, like law enforcement. Privacy concerns around DNA testing are equally important. This is because you are handing over the blueprint of your genetic identity to a private company.
How is your information kept safe?
Businesses that manage customer data are facing increasing scrutiny due to evolving regulations and growing compliance demands. Regulations like the EU’s GDPR (General Data Protection Regulation) ensure that businesses implement strong security measures to safeguard consumer data.
Unlike the EU’s approach, the US relies on a patchwork of data protection laws that vary from one sector to another. Typically, it covers areas such as finance, healthcare, technology, and government-held information, like HIPAA. Although there is a lack of bonding between these areas, some follow regulations similar to those of GDPR more recently.
Companies encrypt your information to ensure data security and fidelity. They encode the data so that unauthorised parties cannot read it.
They achieve this by using TLS and SSL certificates on the domains that support encryption. Moreover, end-to-end encryption has increasingly become popular. In this type of encryption, only the parties involved in communication can read or access the content of messages. However, service vendors can access or read the messages.
While privacy advocates applaud such measures, not everyone is happy. Law enforcement agencies argue that encryption makes it harder to investigate crimes. A political battle has erupted between tech companies and governments pushing for encryption backdoors. Their demand to break end-to-end encryption “for the greater good” seems unrealistic.
So, you should ensure end-to-end encryption whenever applicable.
How can you properly secure your browser?
Internet browsers help you access services online. So, it is a necessity to use a secure browser.
Some of the popular browsers include Microsoft Edge, Apple Safari, Google Chrome, and Mozilla Firefox. Here are some ways to improve security without damaging your online experience.
-
Cookies
Make sure you clean your browser history and cookies regularly. That way, ad networks cannot collect adequate information about your online activity. One of the easiest ways is to clear the cache. (Edge, Safari, Chrome, Firefox, Brave)
To prevent websites from storing cookies, you can set preferences as well. Follow the guides for these browsers: Edge, Safari, Chrome, Firefox, and Brave.
-
HTTPS and HTTP
Whenever you visit a website, you will either see the address start with HTTPS (Hypertext Transfer Protocol Secure) or HTTP (Hypertext Transfer Protocol). The former uses a modern-day encryption technology to secure communication between a server and a browser.
For general browsing, HTTPS is set by default. HTTPS safeguard your payment details from theft and eavesdropping in case you are involved in a financial transaction online.
To see if the HTTPS option is active, look for ‘https://’ in the address bar. You may see a closed padlock in most browsers. Stay away from a website when doing a financial transaction if it does not have an active HTTPS.
In addition, you may consider other secure web browsers or Tor if you want complete anonymity when browsing.
-
Tor Browser
Tor is a non-profit organisation supported by thousands of users worldwide. It has proxy servers that prevent your information from getting compromised. To protect your identity and improve anonymity, the Tor Browser routes internet traffic through multiple layers of encryption.
-
Brave Browser
The Brave Browser is another online tool that provides security and privacy. This Chromium-based browser blocks ad trackers, fingerprinting, and ads to a great extent. Millions of users worldwide use Brave Browser to keep their online activity private.
-
Search engines
Every search engine, including Google, uses algorithms to analyse user data. This is how they deliver customised search results for a better user experience. Browsing history and search queries can build detailed profiles that reveal your online behaviour, preferences, and interests. It poses a risk to your privacy over time.
You should prevent data such as your search queries and browsing history from being logged by an intruder. For that, you can use an alternative that blocks ad trackers and does not store search history. DuckDuckGo is a good alternative you can try.
DuckDuckGo is preferred by users who value online privacy more than anything else. With millions of users around the globe, DuckDuckGo does not sell your information or track you for profit.
Because DuckDuckGo offers a free service, you might be wondering how it makes money. This search engine earns through ads that are shown based on your current search terms. And, not on personal data collected through user tracking that other browsers do.
DuckDuckGo extensions are available on Safari, Edge, Chrome, Firefox, Android, and iOS.
Best browser plugins for improved security
Disconnect – You can block invisible trackers that monitor your online activities and may expose you to harmful content by using Disconnect. It is available for Opera, Safari, Firefox, and Chrome.
NoScript Security Suite – It is a plugin developed for Firefox and other browsers based on Mozilla. NoScript Security Suite disables active content, like JavaScript, that can track your online behaviour.
Privacy Badger – It prevents ad networks from following you. Privacy Badger tracks third parties that monitor users via digital fingerprinting and cookies.
Facebook Container – If you want to prevent social media platforms from monitoring your visits to other sites, you can use Facebook Container. This plugin uses a browser-based container to block Facebook and third parties from tracking you across websites.
AdBlock – It is another useful extension that blocks ads when you are online. AdBlock can block pop-ups, video banners, trackers, and ads to clean up webpages. Moreover, you can whitelist websites if you want the content to show up.
Are public Wi-Fi hotspots safe?
A public Wi-Fi hotspot might appear convenient if you work outside the office. But using one on the go can risk your privacy without proper precautions.
Wi-Fi hotspots are easy to access, both for you and hackers. Therefore, scammers can track your activity to steal your identity. Or, they will divert you to malware-laden websites. Hackers can intercept data sent over public Wi-Fi, including financial details, emails, and login credentials.
Hence, it is unwise to use an unsecured, public Wi-Fi hotspot. Never use such a network to access valuable information, like online banking. The best way is to use a mobile-based cellular connection for more security.
However, if you need an internet connection on a separate device other than your smartphone, use the mobile hotspot option. It is easy to find the option on your smartphone. Connect the device using the hotspot by choosing the name and entering the password that the smartphone has for you.

Using a VPN (virtual private network) is one of the best ways to stay secure on public Wi-Fi. You should use a reliable VPN on all your devices, regardless of the internet connection you have.
What is a VPN, and how does it improve your online security?
A VPN helps create a secure tunnel between web servers and browsers. VPNs encrypt data packets before sending them to destination servers. As such, the location and IP addresses stay hidden. Many VPN services come with a kill switch feature that stops internet access temporarily in case the connection drops.
Many users choose VPN services to view geo-restricted content, such as banned apps and websites. Furthermore, VPNs are a popular choice for activists or in countries governed by censorship.
VPNs are not a complete security solution, but they do help hide your online activity. VPNs help secure connections to prevent tracking and monitoring.
Paid, premium VPN services are more reliable than a free one. The free VPNs usually have lower speeds and less bandwidth. Because operating a VPN service costs money, free VPNs might sell your information.
When a service is free, it is usually the data that is being sold, not the service being given.
Trust is the only thing you need to consider when choosing a VPN service. When you use a VPN, your traffic goes through a third party. If the provider misuses your data, it undermines the very reason for using a VPN in the first place.
Finding a trustworthy VPN provider can be challenging due to factors like conflicts of interest and vague business practices. It becomes even more complicated when providers operate in countries where governments can legally demand access to user data.
How do passwords and vaults keep your information safe?
One of the best ways to secure your online accounts is to use unique, complex passwords.
These days, many websites will prevent you from using simple password combinations, like QWERTY123. These passwords are predictable and could be easily broken. However, using complex passwords for multiple online accounts is challenging. In that case, you need a special tool called a password vault or password manager.
Password managers record your online credentials for every online account. Instead of remembering all your usernames and passwords, a password manager stores them securely in one place. You only need to remember a single master password to access everything. These tools use strong encryption, like AES-256, to keep your information safe from hackers.
Apart from that, password vaults can generate complex and strong passwords for more protection. Also, they can change the weak and old passwords that might be vulnerable.
Password managers and vaults can have some weaknesses, especially if your device is already infected. But overall, using one is still a smart and recommended way to stay secure.
What is the importance of two-factor authentication?
Also called multi-factor authentication and two-step verification, two-factor authentication (2FA) is a popular method widely used. It adds an extra layer of security to your services and accounts, even if you already have a password.
Common authentication methods include SMS codes, biometric data such as iris or fingerprint scans, patterns, PINs, and physical security tools (fobs). Using a two-factor authentication method involves an additional step required to access your data and accounts. Although the method does not guarantee ultimate security, it protects your sensitive information.
Here is how to activate two-factor authentication on popular websites: Microsoft, Google, Apple, Snapchat, Instagram, and Facebook.
What exactly is SIM hijacking?
No denying, two-factor authentication is considered a robust security method to ensure maximum account privacy. Sadly, this security holds no value if you experience SIM hijacking. SIM-swapping happens when a cybercriminal pretends to be you and contacts your mobile provider. They use social engineering tricks to convince the provider to transfer your phone number to a SIM card they control.
After gaining control of your phone number, cybercriminals can take over your accounts and steal two-factor authentication codes.
Unfortunately, this kind of fraudulent activity is hard to protect against. But there is a way to overcome the issue. You can connect the phone number with two-factor authentication to another unknown number. You can even instruct your cellular network provider to reject ownership transfer requests, too. For better results, consider using a security key.
Should you use a physical security key?
A security key is a different type of authentication that relies on hardware. It is an extra layer of protection that cannot be bypassed unless the attacker has the physical key in hand.

A physical security key comes in handy even if an attacker –
- Managed to steal your username and password for one or more online accounts
- Hijacked your phone number to grab two-factor authentication codes
Breaking into your online accounts becomes practically impossible if you use a physical security key. Besides, security keys are affordable these days, and they are easy to use.
How can you secure your mobile devices?
Mobile devices are often used for two-factor authentication (2FA) to help protect your online accounts. However, they can also become the weakest point in your security if compromised. Here are some critical points you should keep in mind.
-
Update phone software
One of the easiest ways to keep your mobile devices private and secure is to check for system updates regularly. By default, every phone activates automatic updates. So, download and install every software update that you receive over time from the phone manufacturer. System updates often include security fixes. To check if your Android device has any software updates, open Settings > Software Update. For iOS devices, open Settings > General > Software Update.
-
Enable device lock
You need to lock your mobile device in any form to prevent it from being compromised. If you are using an Android device, you can choose from a variety of options. These include a password, PIN, or pattern. If you are using an iPad or iPhone, activate the Passcode feature. It will help you create a passcode.
-
Biometrics
Almost every smartphone now comes with biometric-enabled authentication options. These include fingerprints, iris scans, and face recognition. These options are convenient to use. You can access and lock your device conveniently using these options.
-
Find your phone option
In case you have lost your iOS device, the Find My option prevents anyone from using your device. This security feature is available on every Apple device, such as the Mac, Apple Watch, iPad, and iPhone. The feature comes with a remote lock that prevents others from using your device if it is stolen. The Find My Device feature offered by Google lets you call a lost phone, lock it remotely, and erase its data if it has been stolen.
Other useful privacy settings you should know
-
Android
Always disable the option that allows apps from unknown sources. If you have installed an app from outside the Google Play Store, make sure to turn off the “Install Unknown Apps” or “Unknown Sources” setting once you are done. Sideloading apps occasionally isn’t usually a problem. But keeping the option enabled can expose your phone to malicious APK files. It is safer to disable it when you are not actively using it. To deactivate it, go to Settings > Security > Unknown Sources. For the latest Android devices, you can find the option in Settings > Apps > Special Access.
-
iPhone
A useful security feature you get on your iPhone is USB Restricted Mode. It prevents USB accessories from automatically connecting to an iPhone if it remains unlocked for an hour. To enable this feature, go to Settings > Touch ID/Face ID > USB Accessories.
-
Smartphone encryption
You may need to activate the device encryption feature if your smartphone offers one. However, some models will encrypt by default after setting up a lock screen, PIN, or password. If your smartphone’s model supports encryption, go to Settings > Security > Encrypt Device.
Some smartphones have encryption enabled by default, so you cannot see an option to turn it on. However, you can still encrypt SD cards through Settings > Security > Encrypt SD card.
You can also enable the Secure Folder feature in the same settings menu. It will add extra protection to specific folders and files.
-
Jailbreaking
When you root a device, it allows you to install software unavailable on official app stores. Or the apps that need verification from the vendors. However, rooting your device to install unverified software might attract consequences. It will bring an end to your device’s warranty. Additionally, your device will be susceptible to data theft, malicious apps, and malware infestation.
How can you encrypt your messages?
Certain messaging applications include encryption technology to secure online communications.
-
WhatsApp Messenger
WhatsApp is a messaging app that comes with end-to-end encryption. This messaging app offers a straightforward and secure way to chat with either one person or a group. To make the app more secure, go to Chats, select Chat Backup, and disable the option.
-
Facebook Messenger
By default, encryption is deactivated in Facebook Messenger. However, the chat service does have an option called Secret Conversations. Available on both Android and iOS devices, this option has end-to-end encryption. To get started with a secret conversation, select the chat option, tap on the ‘write’ icon, and select ‘Secret’. It will send messages only to the recipients you choose.
-
iMessage
iMessage is a communications platform developed by Apple for iOS and Mac products. This messenger service is another good option if you want to secure your communications digitally. The messages on your device go through encryption using a private key. And, a password is required to access the messages.
-
Telegram
It is another popular application for online communications. Telegram includes a feature called Secret Chat. It has end-to-end encryption to make your conversations private. Moreover, the chats are kept local and not uploaded to the Telegram cloud. These chats are tied to a specific device and come with a self-destruct feature.
-
Signal
More recently, Signal gained a lot of attention because it provides a more secure, accessible messaging service. This free app from Open Whisper Systems comes with end-to-end encryption. As such, the Company’s servers do not store any data.
How do you keep your mobile apps secure?
Regardless of the operating system you are using, downloading apps from a trusted, verified source is always recommended. If you are using an Android device, the Play Store is the best option to download apps. And, if you have an iOS device, the App Store is the right place to download apps. The applications downloaded from these sources help maintain privacy and security.
Apart from that, the permissions you give to an app installed on your device are equally important.
An app can request permissions that give it access to contact lists, messages, call logs, camera, microphone, location, etc. Legitimate apps need access to certain features to function properly. However, it is important to review app permissions so you know what data they can access. This avoids unnecessary security risks or potential data leaks.
For improved security, uninstall the apps that you no longer need.
Is malware designed for mobile devices considered a threat?
Malware for mobile devices does not pose an imminent threat like malicious software does to desktop computers. Still, mobile variants can infect iOS and Android devices to some extent. And in some cases, they can even appear in official app stores.
A common method deployed by malware designers is to make their app appear on the app store as legitimate. After establishing a certain number of users, they upload malicious features to create havoc. For example, the Cerberus Trojan was developed for Android to target mobile phone banking login details. The app was listed on the Play Store.
Different types of mobile malware can hurt your mobile devices. They could be Trojans or backdoors to dubious codes that target valuable information, like banking credentials.
The most common way malware gets onto your smartphone is by installing harmful apps. These apps may look legitimate, but they can be spyware, adware, or other types of malicious software.
Therefore, it is good to have an antivirus installed on your mobile device. Also, you should never root your phone just to use some apps. Download apps only from trusted sources instead of a third-party app store.
Which email service offers the highest level of security?
Many email providers now use TLS to encrypt messages. However, very few email services can be considered fully “secure” because of government surveillance laws, law enforcement access, and the technical challenges of applying strong encryption to inboxes. Absolute security in email remains difficult to guarantee.
ProtonMail is an email service that you can consider trying. The email platform is open-source and operates out of Switzerland. The country’s robust privacy and data protection regulations benefit users. Because of end-to-end encryption, ProtonMail cannot read the emails. Most interestingly, you do not have to provide personal information to create an account.
Still looking for an email service that allows you to send emails while avoiding tracking? Consider using a temporary or disposable email address. You can generate email addresses by using services such as EmailOnDeck and TempMail.
How can you reduce your online footprint?
No doubt, you are going to secure your devices from now on. But you need to think about the personal data already online. Consider what steps you can take to limit future exposure and prevent new leaks.
One of the few things you can do is visit a website that offers a special service. It is a type of search engine that offers services for free. It allows you to check your phone numbers, email accounts, and other linked services for vulnerabilities resulting from data leaks. If you find your information compromised, stop using the passwords involved.
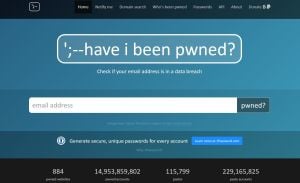
What is the Privacy Check-Up feature offered by Google?
If you use Google services, the Privacy Check-up tool lets you review and manage what data Google saves. You can stop it from storing your search history, YouTube activity, device info, and location check-ins. It also allows you to choose whether or not you want personalised ads based on your information.
Make sure to check your Google Account as well to review and adjust your security and privacy settings. The Security Check-up page also lists third-party apps with access to your account. You can remove any account that you no longer trust or use.
A key feature on this page becomes available if you save passwords in the Chrome browser. Google will review the passwords to find if any one of them is exposed in a data breach. If Google finds one, it will alert you and recommend that you change the password immediately. To simplify the process, each alert includes a link to the affected website or service. This allows you to log in and update your information quickly.
How can you stay safe on social media networks?
Although social media platforms are valuable tools for communication, they could be the main reason for data leaks. It is not just your family and friends who can stalk you across social networks. But also, shady persons or prospective employers might follow you. Hence, it is imperative on your part to lock important information on your accounts. The information that you want others to know should only be made public.
-
TikTok
Because TikTok is popular with young users, it comes with several security settings.
- Restricted Mode and Family Accounts – You can turn on Restricted Mode in your account settings to help filter out content intended for adult or mature audiences. Besides, you can limit screen time, sort select keywords, and so on.
- Private or public accounts – You can choose whether to make your account private or public. Anyone on TikTok can view profiles and videos that belong to a public account. But a private account will limit interactions only to approved users. It is a good idea to enable private settings for accounts used by individuals under 18 to help protect their privacy.
-
Facebook
To lock your account, go to the Settings and Privacy option to make your choice.
- Password and security – In this section, you can enable two-factor authentication and see which devices are logged into your account. Also, you can set up alerts for any unrecognised login attempts. You can assess the strength of your passwords via the privacy checkup option.
- Activity Log – It reviews activity such as messages posted, posts published, likes, and other events. You can erase an older timeline by using the ‘edit’ button.
- Download data – Here, you can download the information that Facebook keeps.
- Profiles, privacy, and tagging – In this section, you can restrict people from seeing your posts. For more privacy, set it to ‘friends only’.
- How people can find and contact you – Make your account stronger by limiting who can see your friends, send you friend requests, and if people can see your phone number or email address. You can also disable the option that allows external search engines to link to your Facebook profile.
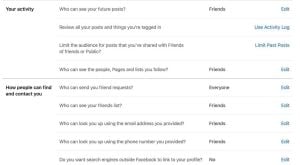
- Ad preferences – You can manage customised ad settings using this option. You can check the interests Facebook assigned to you and which advertisers have your info.
- About Me – You can decide whether to keep your personal information public or private.
-
Twitter (now X)
In the “Settings and account access” tab, you will find several options to enhance your account’s security. However, some options are available only to paid accounts.
- Extra layer of password security – Activating this setting requires additional password reset information. You need an email address or a phone number linked to the account.
- Privacy and safety – In this section, you can alter the information for others. For example, ad preferences, who can contact you, etc
- Two-factor authentication – Using this feature, whether via text messages, authenticator apps, or physical security keys, is only available to paid subscribers.
-
Instagram
If you want improved privacy for your Instagram account, make a few key adjustments to your settings.
Anyone visiting your Instagram profile can view the videos and photos. However, you can change the default setting to one that suits your requirements. Go to Settings and choose Account Privacy. You can adjust this setting so that only approved followers can view your content.
If your profile is set to public, anyone can engage with or view your videos and images. Furthermore, you can block users whom you do not want to interact with.
What is the right way to secure your Internet of Things devices?
Smartphones, tablet PCs, and smartwatches are the mobile devices that implemented the Internet of Things (IoT) first. As of now, home hubs to smart speakers and smart lights, that is almost every smart device, have IoT. For example, Amazon and Google Home.
For improved security on these devices, make sure you take the following steps.
- Increase network security
- Lower the attack surface
- Assess unpatched vulnerabilities
- Opt for a comprehensive IoT security solution
Do tracking devices pose security risks?
Certain products, such as Apple’s AirTag and Tile, could be convenient ways to keep an eye on your keys, luggage, pets, and other belongings. However, the networks and Bluetooth technology that enable this service can be abused by cybercriminals.
Tracker devices have reportedly been linked to incidents of stalking and even car theft. These devices are small enough to be hidden in a bag, clothing, or a vehicle without being noticed. Even if a victim suspects they are being tracked, locating the device can be difficult. So, it leaves them wondering what to do next.
Solutions to these problems are still in development and gradually being introduced. Apple users who have iOS devices (version 14.5 and above) are now alerted via sound and notification. For Android devices, the Tracker Detect app alerts users of such instances.
Who holds the responsibility for safeguarding your privacy?
The threats to your privacy and security are constantly evolving. As it appears, within just a few years, things can improve or deteriorate. When it comes to encryption, it is an ongoing tug-of-war between governments and tech giants. Cyber attackers are constantly developing new methods to exploit individuals. Meanwhile, some governments prioritise control over protecting personal privacy.
As remote work becomes more common, studies show that cyber incidents are increasing. Many people remain unaware of essential security practices. Without taking basic precautions, you could be putting both your devices and your company’s systems at risk.
Fortunately, privacy and security threats have now been addressed by technology companies. Several organisations, both non-profit and profit, took the responsibility to develop and implement tools that benefit users at large. With these intuitive tools, you can drastically improve your security and improve your online experience. But, whether or not to use them relies upon the users.