Onion Over VPN: What It Is
Onion Over VPN is an intuitive technology that focuses mainly on privacy by adding different layers of security. That way, unauthorized third parties cannot access the online activities of users. This technology works in cohesion with a VPN (Virtual Private Network) and Onion Router (or TOR). Let’s understand them in detail.
TOR is a specialized network that provides anonymity to internet traffic. It does this by routing the traffic through several nodes. As such, no one can trace back the actual path of a user. Keep in mind that TOR does not encrypt traffic. Also, it does not protect users against online threats. This is when VPN comes to the rescue.
A VPN works as an encryption tunnel that acts between specific VPN servers and users’ devices. That way. No one can intercept or view users’ online activities. When VPN is combined with TOR, it results in Onion Over VPN. This tool comes with the benefits of both technologies. Users can enjoy the security aspects of a VPN and the anonymity that TOR delivers.
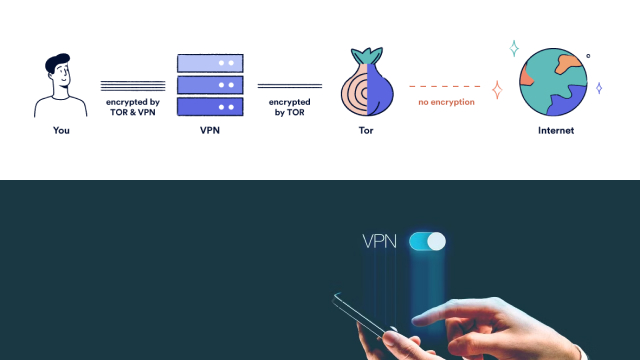
Whenever a user connects to the internet using Onion Over VPN, the traffic first reaches the VPN servers. Later, it enters TOR. Even with a compromised TOR network, the location and IP address of a user stays undetected.
For users who seek maximum security and privacy for their online activities, choose Onion Over VPN.
Onion Over VPN: How It Works
To begin with, Onion Over VPN combines the benefits of VPN’s security features and TOR’s encryption features. This technology routes the internet traffic of a user through specific VPN servers before entering TOR.
Whenever users connect to the internet using Onion Over VPN, the traffic reaches a VPN server after proper encryption. Next, it goes to TOR where the traffic moves through several nodes. Each node adds different layers of encryption. The process goes on until the traffic reaches the last node. This is where the data is decrypted before moving on to the specific destination.
Onion Over VPN has additional layers of security and privacy. The internet traffic first goes to the VPN before making its way to the TOR network. The VPN encrypts internet traffic thereby protecting users against potential online threats. Whereas, TOR provides anonymity by concealing the users’ locations and IP addresses.
In short, Onion Over VPN is a powerful tool that combines security and privacy features. Users who seek maximum protection during online activities prefer Onion Over VPN.
Benefits of Using Onion Over VPN
For users who are looking for increased security and privacy online, Onion Over VPN has several benefits. Check out the benefits below.
-
Security
With encrypted internet traffic, Onion Over VPN protects users from hackers and other kinds of online threats. Besides, it prevents ISPs from throttling or monitoring internet traffic.
-
Anonymity
Combining VPN and TOR, Onion Over VPN provides users with added layers of anonymity. Third parties cannot get the location and IP addresses of users. And, they cannot track the online activities of users.
-
Accessible restricted content
The users’ locations and IP addresses are not visible when using Onion Over VPN. As such, it allows users to view web content that comes with geo-restriction policies. A user can view restricted content easily.
-
Ultimate peace
Users feel delighted when they are aware that no one can trace back their online actions. Onion Over VPN safeguards the privacy and security of users efficiently.

In conclusion, Onion Over VPN should be the best option for anyone who seeks improved security and privacy during online activities. It combines the VPN’s encryption feature with TOR’s anonymity feature to provide a robust solution in terms of online security and privacy.
Onion Over VPN: How to Set It Up
Onion Over VPN requires easy steps to complete installation. Follow the simple steps to install it.
-
Downloading and installing TOR
First, download TOR and install the same on the device’s browser. Anyone can use TOR on their Linux, Mac, or Windows computer.
-
Choose the VPN provider
Choose a provider that has support for Onion Over VPN. Remember that not every VPN provider has support for this feature. Therefore, make sure before heading to the sign-up section.
-
Connecting to the VPN
After choosing the right VPN, connect it to the desired server. It prevents unwanted cyber threats because of the encrypted internet traffic.
-
Activating Onion Over VPN
Almost every provider that has support for Onion Over VPN includes an option to activate the feature. Look for settings within the VPN client. Enabling this feature will result in secured internet traffic. Both VPN and TOR route the internet traffic.
-
Testing the connection
After activating the Onion Over VPN feature, it’s time to test the connection. It ensures that the feature is working fine. Visit a specific website where it checks the location and IP address of a user.
By following the above-mentioned steps, anyone can set up this innovative technology to enjoy improved security and privacy online.
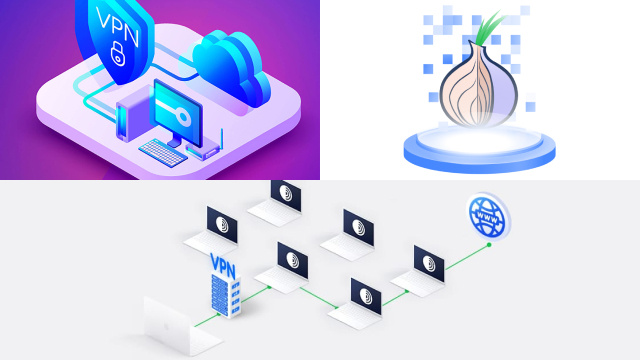
Difference between Onion Over VPN and Traditional VPN
Both Onion Over VPN and traditional VPN are powerful tools that provide improved security and privacy to users. Still, there are significant differences between these two features.
The main difference between the two is the combined feature that a VPN and TOR provides. VPN has security and encryption features whereas TOR provides anonymity. When users use Onion Over VPN, it provides an additional layer of security and privacy. Third parties cannot monitor or trace back users’ online activities.
On the other hand, traditional VPNs encrypt and protect internet traffic from unauthorized access. Unlike Onion Over VPN, traditional VPNs do not provide similar anonymity. That’s because the VPN servers can identify the real location and IP address of a user.

There is another big difference between Onion Over VPN and traditional VPNs. Because of extra routing, Onion Over VPN works slower than traditional VPNs. However, the slow connection is not a matter of botheration for some users. They prioritize privacy and anonymity over speed.
Both these technologies offer innovative tools needed for security and privacy online. Choosing between traditional VPNs and Onion Over VPN depends on the priorities and needs of an individual.
Security Features of Onion Over VPN
To protect the online activities of a user, Onion Over VPN includes a variety of security features. The encryption feature routes the internet traffic of a user through the VPN server. Potential hackers cannot read the encrypted data. Encryption protects sensitive data such as credit card details, passwords, and other personal information.
Anonymity is another feature that hides the location and IP address of a user. Onion Over VPN routes the traffic through TOR making it hard for intruders to monitor the online activities of users.
Additionally, Onion Over VPN protects users from cyberattacks such as malware, phishing, and hacking. Attackers cannot install malware or access sensitive information thanks to masked IP addresses and internet traffic.
Onion Over VPN offers stringent security features that protect the online activities of users. It’s a powerful tool that improves online security and privacy.
Onion Over VPN: What Future Holds
Onion Over VPN has a promising future. The need for online security and privacy is increasingly becoming popular among users globally. Because more people are looking for ways to secure their activities online, the demand for advanced security features will be on the rise. In this regard, Onion Over VPN will grow continuously.
In the era of machine learning and artificial intelligence, Onion Over VPN has made significant developments as well. These technologies can improve the functionalities of Onion Over VPN. It can identify and block potential cyber threats efficiently.
More recently, blockchain has emerged as a breakthrough technology. If Onion Over VPN leverages the transparency and security that blockchain provides, users can have the highest level of privacy and security.
No wonder, Governments all over the world implement censorship and surveillance measures. In that case, Onion Over VPN can become one of the essential tools for increased security when online. With the rising demand for online security and privacy, continued development and growth in this area are predicted.
Is Onion Over VPN the Right Choice for You?
By now you have understood that Onion Over VPN provides improved security and privacy for online activities. The security and encryption features of a VPN along with the anonymity of a TOR network make Onion Over VPN a powerful tool. It offers online protection at a higher level for users who seek privacy and security.
It depends on your priorities whether or not to use Onion Over VPN. If you value privacy and anonymity over speed, Onion Over VPN is the right choice for you. If you prioritize speed over privacy, choose one of the traditional VPNs available at hand.
Keep in mind that Onion Over VPN might not be the best solution even if it has additional privacy and security features. You have to take precautions whenever you are online. Never visit suspicious websites and use strong passwords. Also, keep your software and devices updated.
Whether you want to use Onion Over VPN or other tools that provide online security depends on your specific needs. Therefore, evaluate your requirements and choose accordingly.